Halo 2: Gateway to a Security Career
Back in late 2004, Bungie rocked the world of online gaming with the launch of Halo 2 for the Xbox.
This was before cloud computing was mainstream, and hosting dedicated physical servers was an expensive task, so many developers (including Bungie) chose to go with the cheaper option - a distributed networking architecture. The architecture is simple: one client is chosen to be the game server (referred to as the “host” for the rest of the blog) and the other client would connect to it as the source for the current state. When things like latency issues arise between clients, the host’s version would be the one that is taken as the official record.
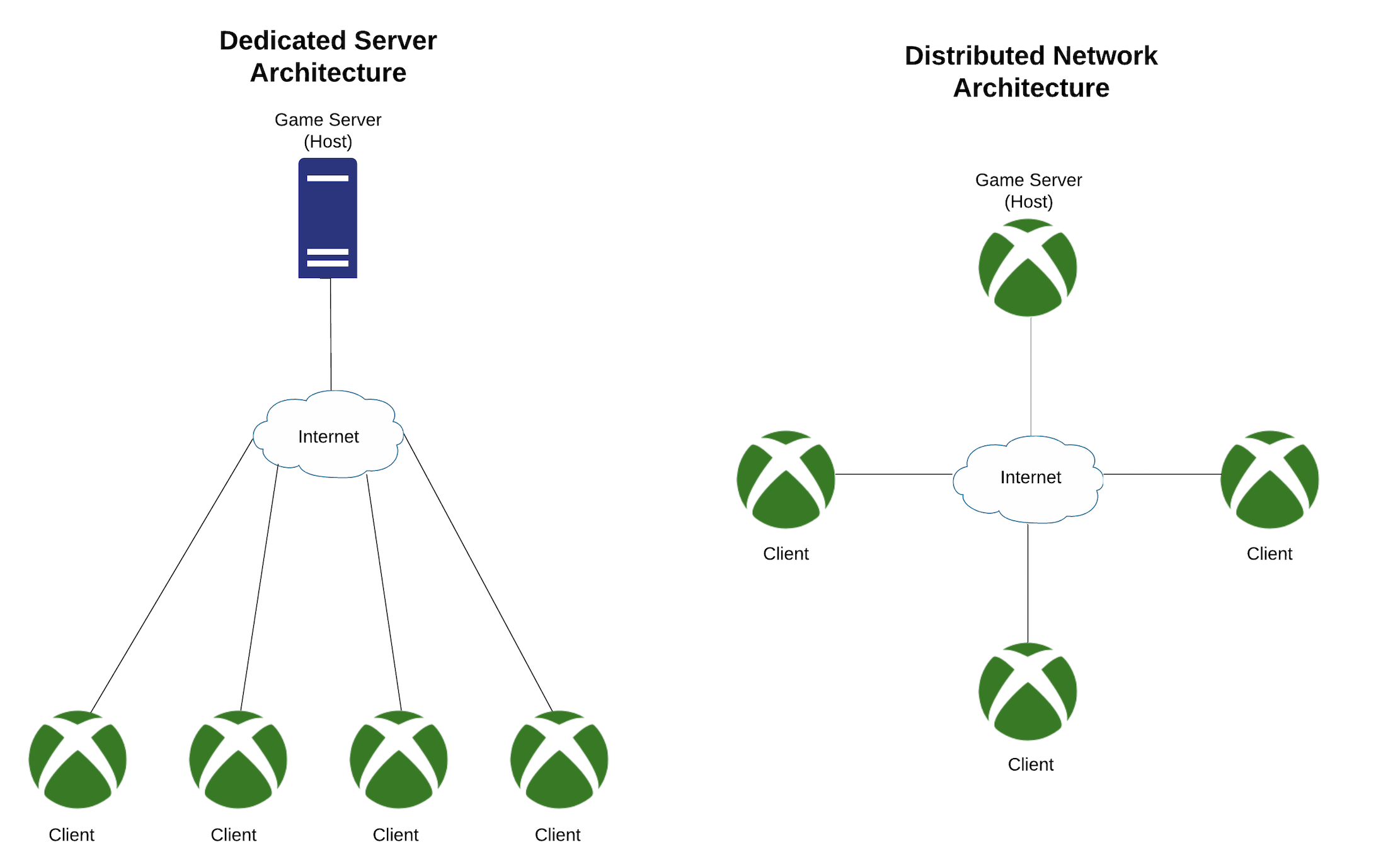
This allowed for some pretty interesting exploits, the most famous being a network manipulation bug known as “standbying.”
The name “standbying” comes from the standby button on many older modems. When pressed, all network connections are effectively paused until the standby button is released. When the host presses standby, they have about 8 seconds to resume connectivity otherwise Halo would treat this as a connection failure, kick them out of the game, and choose a new host.
During that 8 seconds, all of the other players would be sent to the infamous “blue screen” while their character would remain in game. The host would then be able to kill those players, capture the flag, board their ghosts - whatever they pleased!
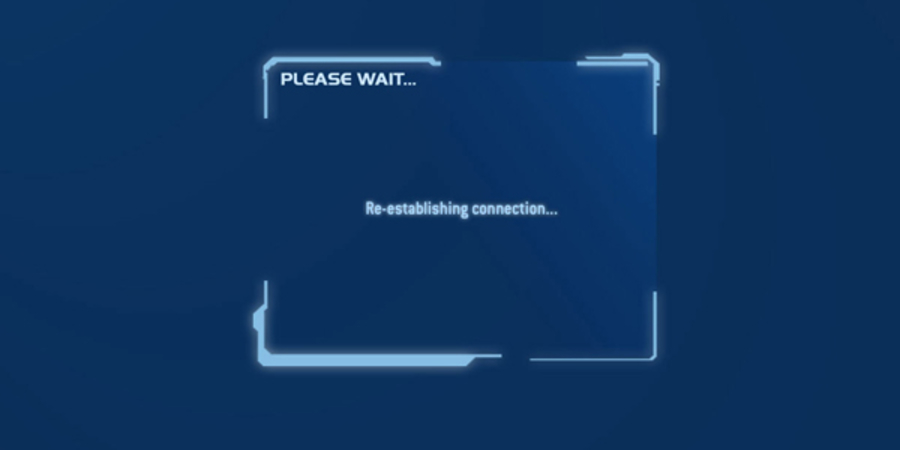 Halo 2 Blue Screen
Halo 2 Blue Screen
At the 6th or 7th second, the host would resume their connection and all players would reconnect, finding themselves respawning or worse, the game ending in a loss.
I first experienced this when my friend accidentally hit the standby button on the modem when we happened to be host and saw all of the players start running into walls. We were able to keep playing for the 8 second grace period before we were booted from the game for connection issues.
This is where you can imagine 2 middle schoolers with light bulbs popping up over their heads.
After quickly reconnecting everything and trying again, it didn’t work. I realized we needed a solution that would allow us to ensure we were the host every time and also prevent us from getting kicked from the game for connection issues. We hit the drawing board and got to work on an ingenious, but hacky, solution.
Note: I do not condone cheating, but this was both fun and educational!
The Setup
The architecture needed to satisfy 3 requirements:
- The ability to sniff and filter both ingress/egress network traffic for the host Xbox
- Enabling/disabling the “standbying” action needed to be automated
- My Xbox had to be chosen as the host 100% of the time
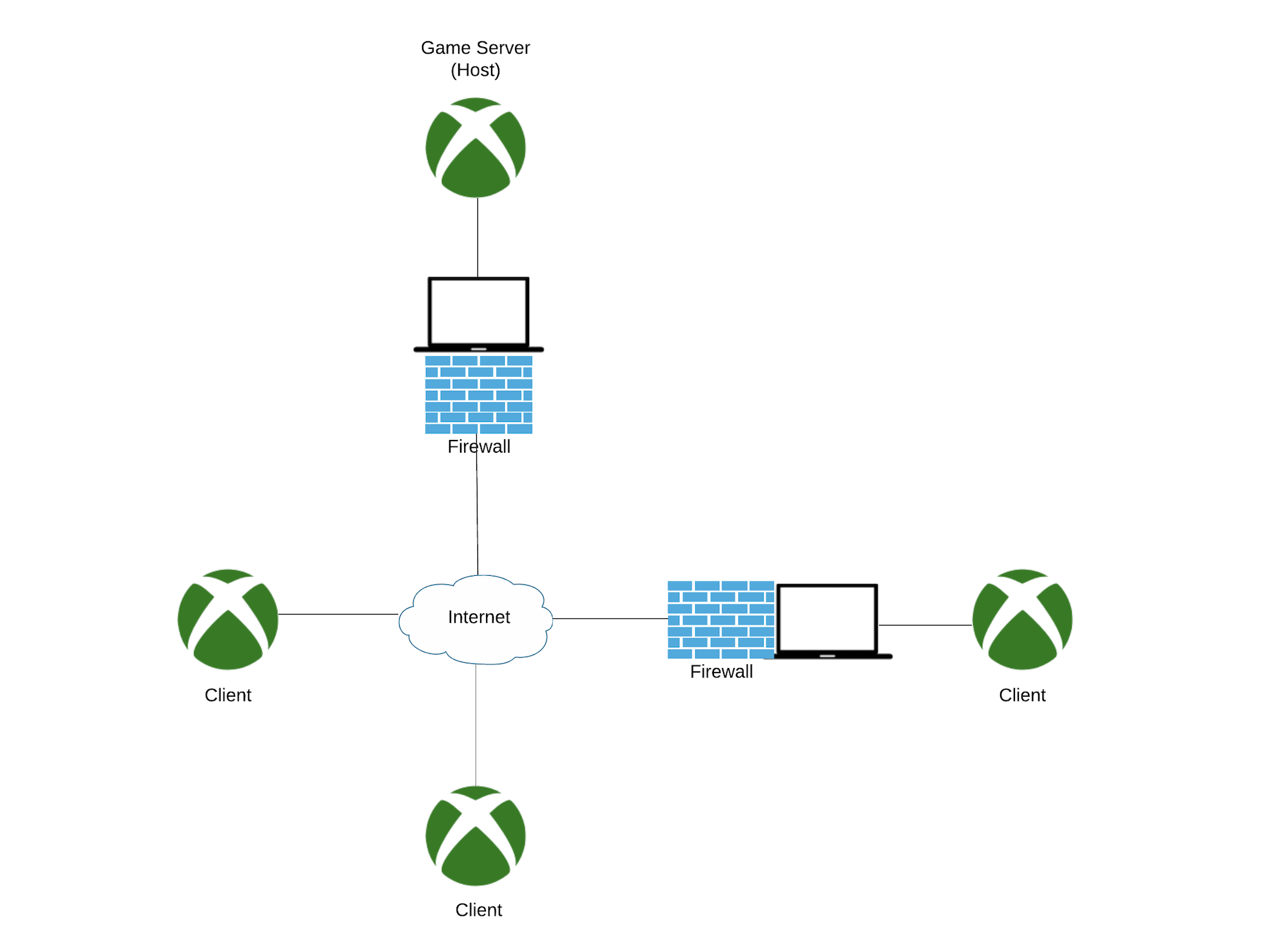
To meet the first requirement, I decided to install a second ethernet card in an old laptop with one Cat5 cable to the router and the other to the Xbox. This gave us the ability to bridge the connections, using built in Windows XP features, so that all traffic between the host Xbox and the router would be accessible to the laptop operating system. Once configured, I tested the connectivity from the Xbox. Success!
Now that we had a device that was acting as a MITM (man-in-the-middle), we needed software to sniff and filter the network traffic. Making only $10/week allowance doing yard work meant that the solution needed to be free. This is where we found ZoneAlarm. The free version allowed you to whitelist and blacklist IPs so we went with it. Side note: I checked it out - ZoneAlarm still exists!
Also installed on the laptop was a program named CommView which was designed for network admins to sniff ingress and egress traffic. When in a match, Commview would list the IPs of all of the other players. By taking these remote IPs and plugging them into the ZoneAlarm blacklist, we had the ability to send anyone in the game to the blue screen, or kick them out of the game completely. Disable ZoneAlarm, and they immediately reconnected. Win \o/
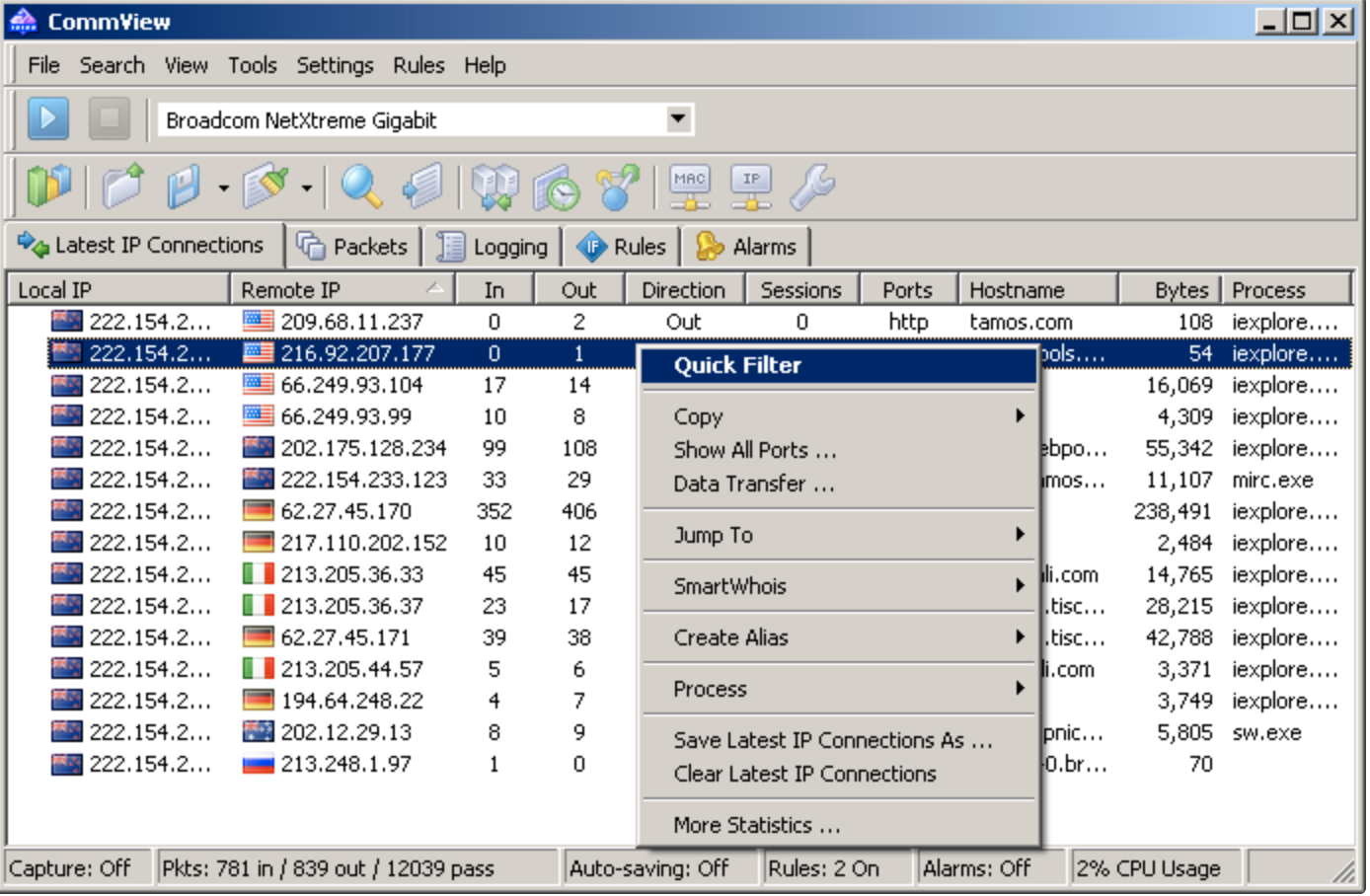 Due to CommView now costing $299/license, here’s a screenshot from their website.
Due to CommView now costing $299/license, here’s a screenshot from their website.
To meet the second requirement, my teammates were added to the ZoneAlarm whitelist and opponents to the blacklist. Then we configured a free mouse macro tool named EZ Macros to repeatedly enable and then disable the firewall rules every 6 seconds (extremely hacky, but it worked). This was the perfect amount of time to ensure that all of the other players remained in the blue screen for a majority of the game without us getting kicked out.
To meet the final requirement, I needed a partner in crime. We noticed that if any of the players in the party were unable to establish a connection with the chosen host, the entire party would be sent back in the queue to search again. In order to ensure that I was always the game host, one of my friends needed to bridge their connection and use ZoneAlarm to restrict outbound traffic to my Xbox only. This way, the search would continue to restart until we found a game where my Xbox was host.
It was a huge success! We entered game after game, let the macros run and watched as all of the other players would be walking into walls while we captured the flags, assaulted the enemy bases, and won every time.
Believe it or not, all of those times I stayed up late playing video games I was actually learning. I think even my parents finally believe me. This experience tipped over the first domino that led me to an interest in network design and an understanding that even simple architecture decisions can be exploited. 16 years later I find myself thinking about security for a good chunk of every day. Whenever I am asked “what got you interested in security?” I think of Halo 2.